And now, from the end-user POV of I2P.
In a previous article, we also thought about the NotBob review. Our experience was setting up I2P on our VPS so that we could share our website on another alternative network out there. After all, with our moderate success with .onion/Tor networks. Why stop there?
We think that article was so focused on setting up "i2pd," which is a Java-less version of the i2p gateway software. perfect for hosting on VPS systems, which may have restrictive amounts of RAM or single-board machines. That we never really set up "I2P' as a client, instead, rely on the self-contained client downloads from the i2p-project webpage. In the past, it was criticized for being a little hard to use, and when using a Windows machine. The software is getting flagged by virus checkers.
It's time to set up our home client correctly now. Or at least in our view of what "Correct" is. Read on to listen to my diatribes on this.
First off, what the hell is I2P?
Party people, we have to do this. Because you never know if this is the first time someone is reading about this or someone who's been around the net a long time!
Project page is over here. But the short description of this is alternative networking. Unlike the clear-net, you have to pay for a domain, and have a static IP address so that the DNS servers can resolve the name of your domain. Pay for SSL. Pay to hide your identity on SSL so your mailbox doesn't get filled with scams trying to steal your domain. And so on. I2P You simply register your address. Keep the router going, and host a website. Or! Jump on other services like IRC, or even torrent file transfers.
This is crazy blockchain shit, right?
It's not a Web3 scam where you have to invest in crypto to get a domain. Only to find out that you're now bound to the site that gave you the domain to change it. Or there may not be a single website that is using the blockchain you purchased a domain on!
There are many like it. But this one is mine.
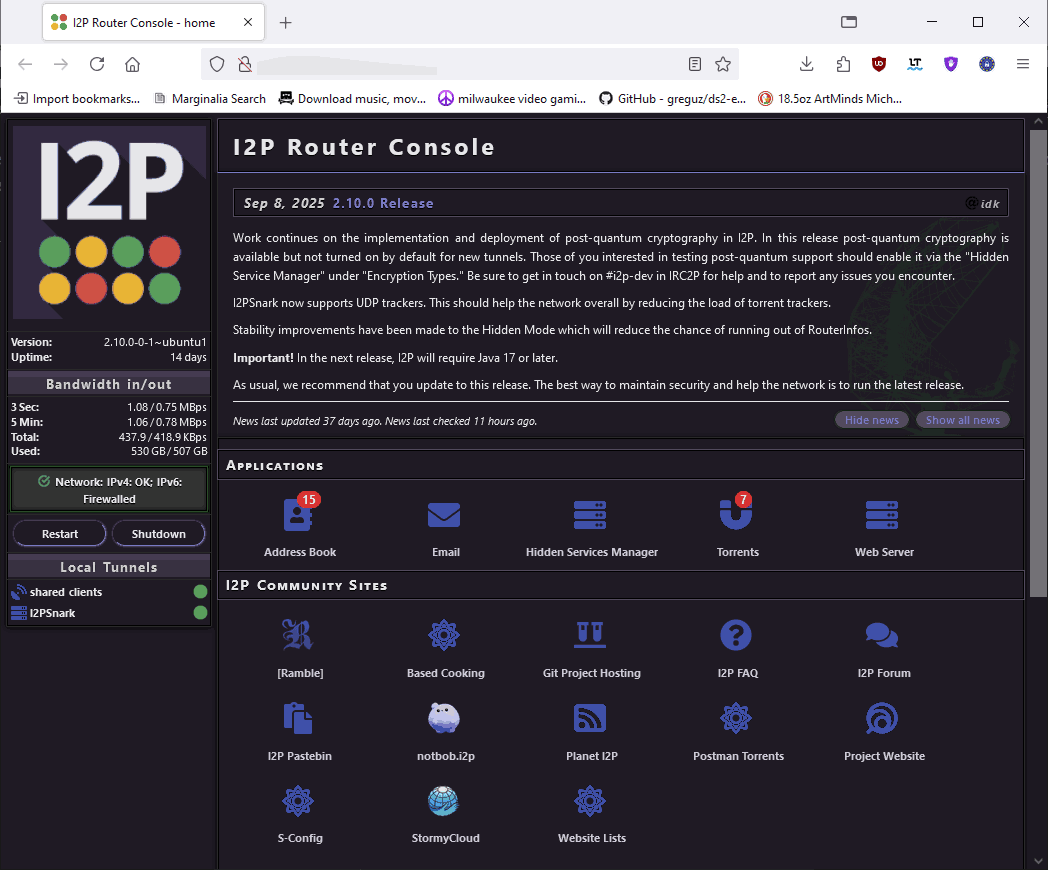
To the average person who uses I2P. What the fuck are we saying? There is no such user on I2P that's anywhere close to 'average'. Take that as an insult or a compliment. It's just the truth. No normal person sits down and says:
You know, I think I'll fuck with my browsers proxy settings and install router software locally so I can visit an alternative network. - Anonymous
Some would argue that this is a 'feature' as it would keep less experienced internet users off their proverbial front lawn. But back on track.
This is usually what you are greeted with after installing the Java I2P software directly from the project homepage, except for one key component.
It's not pointing to 127.0.0.1 or loopback.
When you install the I2P software, everything loops back on itself as a security precaution. Meaning, all of the interaction between the browser and I2P is handled locally. This router website cannot be accessed even across the LAN. In its very name, "I2P Router Console," is not software that sits on your laptop or desktop. Especially in a home environment. This kind of software should sit on an appliance that is on 24/7.
In our scenario:

Referencing another blog about using $10 thin clients instead of Raspberry Pi's. We already have one of these bad boys on 24/7 acting as an OpenMediaServer with a 500GB M.2 drive installed. With 8GB of RAM, it also has plenty of space to run the full Java I2P system. To put I2P onto an appliance does a few things:
- It offloads a lot of the work I2P does onto another box.
- By it staying alive 24/7 and adjusting my data to whatever I'm comfortable with. It also helps improve the I2P network, acting as a tunnel for encrypted traffic to pass right on through.
- If you're going to be poking holes in your firewall (under configuration > network) to get the best out of the I2P network, we would rather do this to a box that has a static PC than a client with a dynamic one. (Especially if you're dealing with a shit router with no UPnP, which is an additional thing we would probably fix in our home)
Right! Since the static IP was already set up on a box like this running Debian, which we followed, I2P's instructions to find a mirror to download from. It's just a matter of loading the software and changing the IP in the beautiful website that was given to us.
So, it's just a matter of sudo'ing your I2P service
sudo apt-get install i2p i2p-keyring systemctl enable i2p systemctl start i2p
Right?
Well! Not so much.
 The hidden services manager.
The hidden services manager.
Although it's possible to modify the services themselves to allow an IP address of someone in my LAN to access the I2P network via browser using network proxies. That's not going to change the IP address of the router's website.
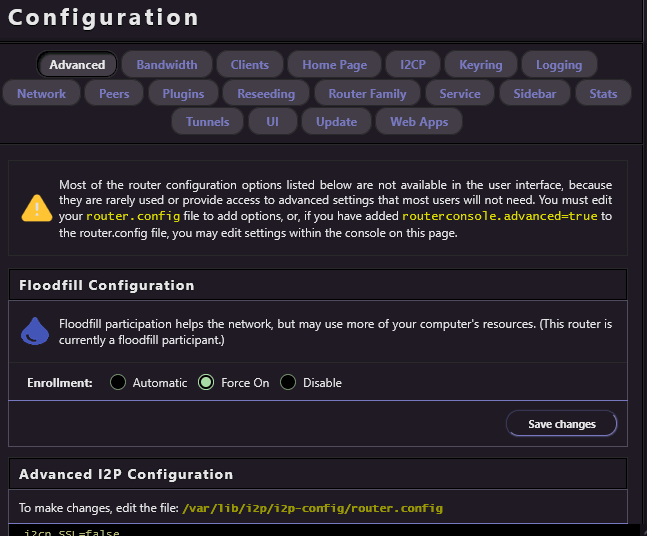
The advanced settings at least give you a hint as to where your configuration file is.. But unfortunately, not everything is in /var/lib/i2p/i2p-config/router.config
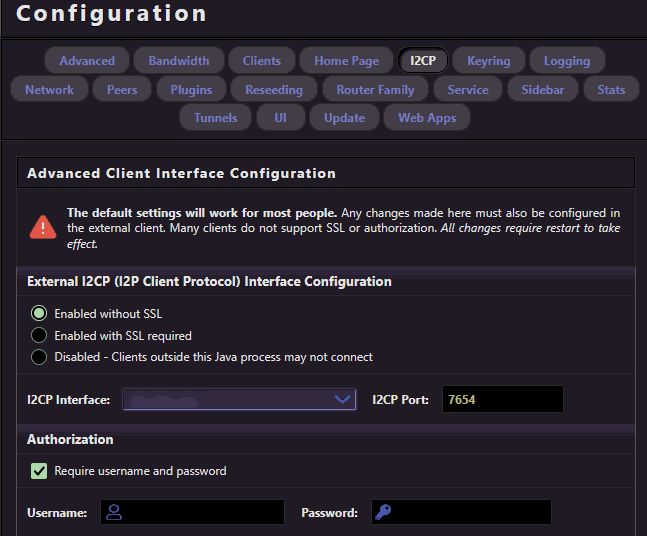
Now, you would THINK the I2P website would allow you to change the I2CP interface and port to whatever IP you want. Restart the router services, and then you're ready to access it anywhere on your LAN. Also, as a precaution, set up a username and password just in case things get stupid.
But it didn't work for us.
We had to go into /var/lib/i2p/i2p-config/clients.config.d/00-net.i2p.router.web.RouterConsoleRunner-clients.config
Then we start modifying IP addresses (with our changes highlighted in bold):
# NOTE: This I2P config file must use UTF-8 encoding # Last saved: Aug 2, 2025, 5:22 AM clientApp.0.args=7657 ::1,10.10.0.253 ./webapps/ clientApp.0.delay=0 clientApp.0.main=net.i2p.router.web.RouterConsoleRunner clientApp.0.name=I2P Router Console clientApp.0.startOnLoad=true
We're not entirely sure if this is an isolated incident or just the nature of us running I2P as a default service on bootup. But it wasn't very pleasant that there were multiple configuration files inside of I2P and not all of them synchronized to the webpage.
systemctl restart i2p
after all of that fun stuff, now we can access the website anywhere within our LAN, just like a router service should be.
It's just a matter of setting up a dedicated browser to go off to I2P like a nightly build of Firefox.
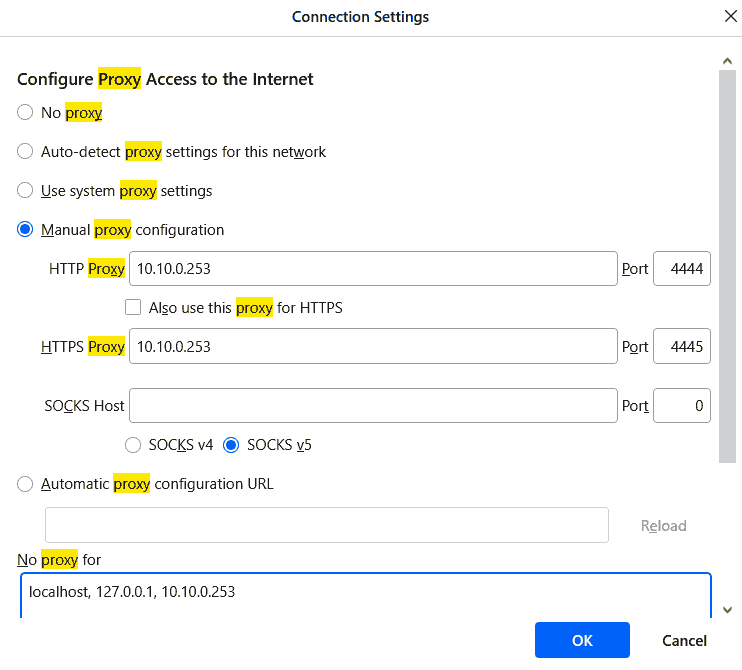 Screenshot of proxy setting setup within Firefox
Screenshot of proxy setting setup within Firefox
As mentioned before in our previous blog on I2P. This part is probably where your entry-level internet user would feel very uncertain about doing. Which is diving into your browser settings. Changing the proxy configuration of their network connection to point to the I2P router (127.0.0.1 would be the default installation), but because of what we have done, we can route this to our T6t20 thin-client box.
You could argue that limiting your browser experience to just the I2P network is frustratingly slow and does not integrate well with clear-net services like Tor does. From a security standpoint, if you're on the alt-net, you want to keep your browser always connecting to the alt-net. Because all it takes to get your IP discovered is if an I2P server sends an HTTP request to look up an image (as an example) on the clearnet, and people would know you've visited their server.
Also, super important to put the IP of your router into the "No Proxy" list, or else you can't reach the site.
Address book time.
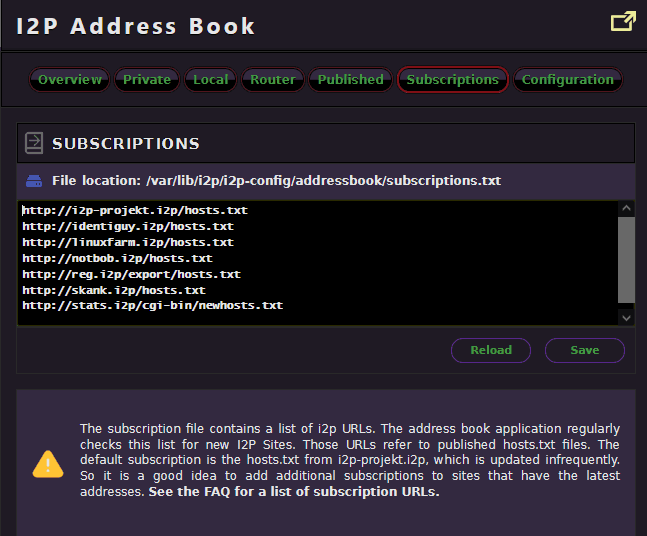
Another thing that we like to do with our I2P Router is add as many host.txt address books as possible. As these would be the way you can resolve vanity name addresses like s-config.i2p, instead of typing in the base32 address that we posted within our mirrors. i2p-projekt.i2p is there by default, but sometimes does not contain the newest addresses.
For that, we add the rest.
http://identiguy.i2p/hosts.txt http://linuxfarm.i2p/hosts.txt http://notbob.i2p/hosts.txt http://reg.i2p/export/hosts.txt http://skank.i2p/hosts.txt http://stats.i2p/cgi-bin/newhosts.txt
Then hit the save button. (Please note this was published August 15th, 2025, so addresses may be changed/added/removed after this date.) This is actually how the start of the internet was, before the concept of a primary DNS server even became a thing. Just address books of vanity domain names that everyone sort of agreed upon.
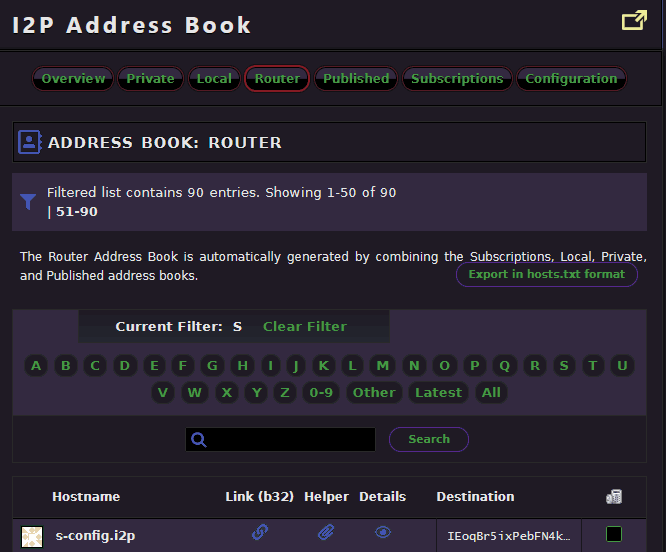
Within a few minutes, you'll find out that there are about 1,000 listed websites that you could view in I2P. Which we know what you, the reader of the internet, may be thinking.
Wow, that's unimpressive. - Anonymous.
In which you would be correct. But also understand these are just the published I2P addresses. You could run an I2P site and not publish a vanity DNS, thereby you're mostly hidden from the public eye.
Other services.
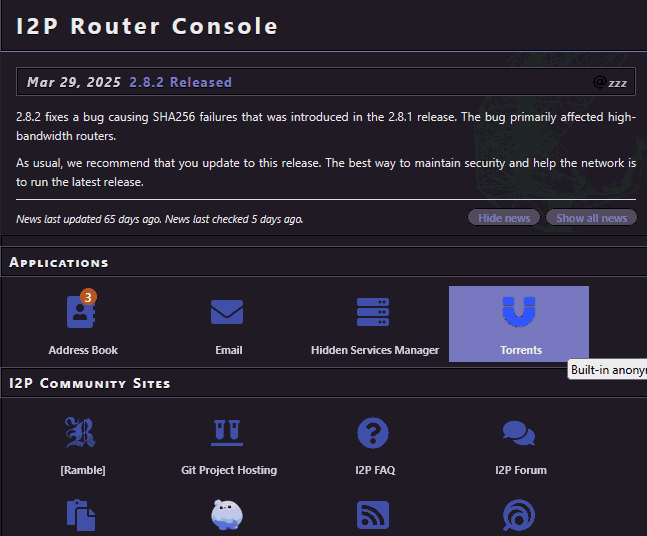
Web browsing is not the only thing you can do with the I2P network. There's Email, which, if the I2P network were a little bigger, we would suppose we would enable that to receive messages from that. However, the best feature of the I2P network realistically is the Torrents system, which takes you over to a utility known as I2PSnark.
This part of your router allows you to not only participate in torrents within the I2P network. But also create them. Def-Con has taught me that nothing is unbreakable. However, I2P is, in our opinion, an alternative to paying for a VPS that could easily turn you over to the government by providing logs of what you do, even though many of these VPS providers pinky-swear that they won't. There is absolutely no guarantee that if force is used, they will comply. Some of them happily. One of the many reasons why we dropped our NordVPN partnership.
One of the reasons why I2PSnark is integrated into this network is that a website may wish to offer large binaries to someone. Using a web browser to download normally may be problematic at best, with I2P's latency issues being dependent on how many hops between bridges it may take. Torrents are more resilient when it comes to latency and time-out issues.
Another rule of using I2PSnark is that you have to get a magnet link from an I2P website. After a while of looking at various lists and places. tracker2.postman.i2p.
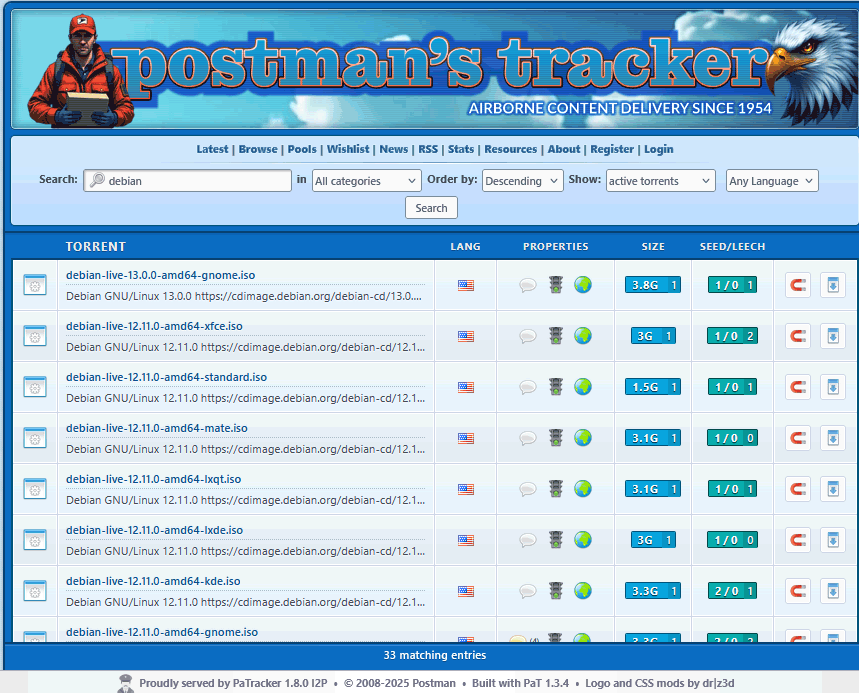
What you search for on Postman is entirely up to you. But you'll find a few things a little different than searching on a site like Pirates Bay.
- Selection is limited due to the scale of the I2P network.
- Seed/Leech count is also limited because of the scale of the I2P network.
- Because it doesn't talk to the clear-net. An identical torrent that exists on the clearnet will most likely have more participation at the cost of losing your IP Privacy without a VPN service.
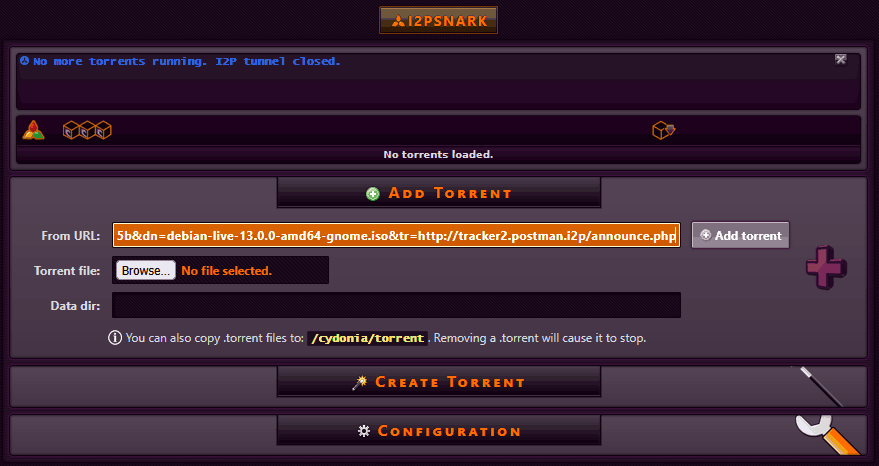
Usage is fairly straightforward. Copy the magnet link, go back to I2PSnark, and paste it. Alternatively, you can download the torrent file itself and upload it to I2PSnark as well.
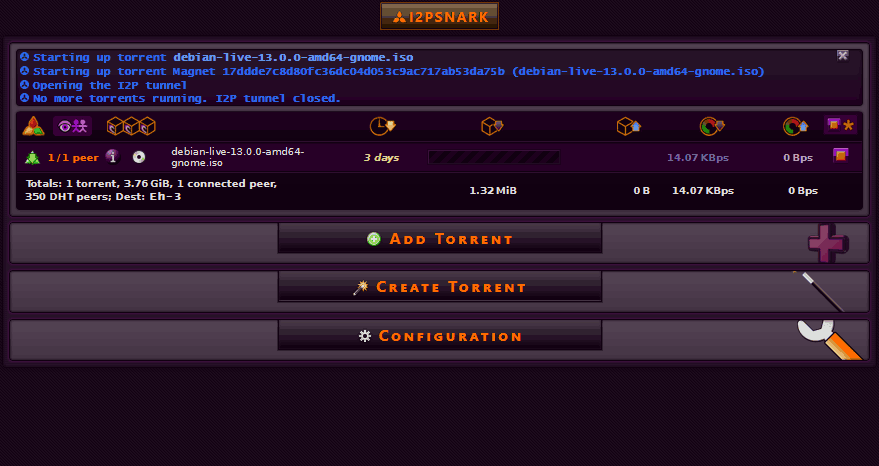
After that, your appliance goes to work downloading the torrent. More seeds also means a faster download, as we've seen transfers spike up to 2MB/sec in speeds. Again, I2P is not a fast network. It's designed to try and anonymize you.
Final thoughts.
We pride ourselves on being the kind of bloggers who not only write about technology but also use it as well. With the router software installed on an appliance PC that is used for many other services, while at the same time helping the network grow.
We have also been seeing some fluctuations within hidden services, such as a reduction in Tor but a steady increase in I2P-related traffic. The logs, of course, do not pinpoint where this traffic is coming from. Just that "It's happening," and for the most part, there are no errors. Part of this may be drama that happened within the Tor network, such as the German police setting up a bunch of nodes to try and deanonymize people. To which we thank you for your bandwidth, Germany. Tor is just another medium of communication to us, just like I2P is as well. But we think the Tor Project also would thank Germany for pointing out the flaw in their software in which they have corrected.
As for our network status of "IPv6 Firewalled." I played with this setting a lot and found that we could only get either IPv4 set to 'OK' or IPv6. Not both despite the port status from the router to the appliance box being opened. Again, we think it's because of our shit routers' lack of UPnP protocols, which is why we can't get 'OK' across the board.
As far as stability.. It's about 95%. Sometimes I2P will shit itself 404'ing out when looking up vanity IP addresses. But if you hit refresh again, the site comes back up normally. Identical to Tor as well. All traffic appears to be unencrypted HTTP traffic, which freaks out certain users. Google, after all, beat it into everyone's heads that you gotta have HTTPS all the time or else the world would end. With I2P, it's not required as the protocol does the end-to-end encryption for you. How much you, the user, trust is entirely up to you.
Thank you for reading. Until next time.
That's what server said.
+++END OF LINE